
Building a fortress: Understanding Defense In Depth in InfoSec
The principle of defense in depth (layered defense, in-depth defense or layered security) is a fundamental principle[…]

Flipper Zero: Signal jamming
In one of the previous posts we’ve looked at capturing sub-GHz signals. Today we’re going to look[…]

Why scanning random QR codes is a bad idea
QR codes have become an integral part of our lives, offering convenient ways to access information, connect[…]

PowerShell: Exfiltrating data to Discord
What is Data Exfiltration? Data exfiltration refers to the unauthorized transfer of data from a target system[…]
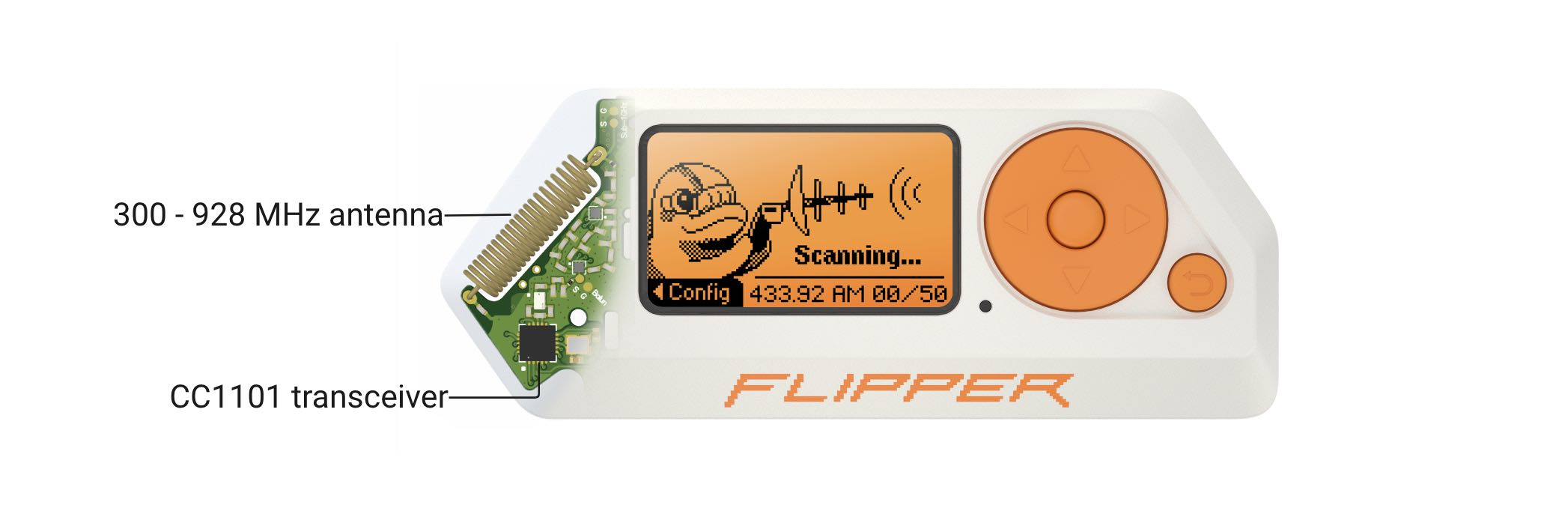
Flipper Zero: Capturing and replaying Sub-GHz signals
The Flipper Zero is a versatile pentesting device designed for various security testing and hardware hacking tasks.[…]

Flipper Zero: How to install a custom firmware
Why would you install another firmware? When you own a Flipper Zero, there are several reasons why[…]

Flipper Zero: How something simple as Bluetooth can get you hacked…
Nowadays we all use Bluetooth on our devices. This allows us to connect to smartwatches, the audio[…]

Exploring Flipper Zero: A “Revolutionary” Device in Cybersecurity
In the ever-evolving landscape of cybersecurity, innovative tools and technologies continually emerge to address the escalating challenges[…]

Flipper Zero: Ban or not?
“In just a few years, Flipper Zero has become so popular that it’s now surrounded by many[…]